ReRAM Applications: Crypto Wallets
Hardware-rooted protection for digital assets
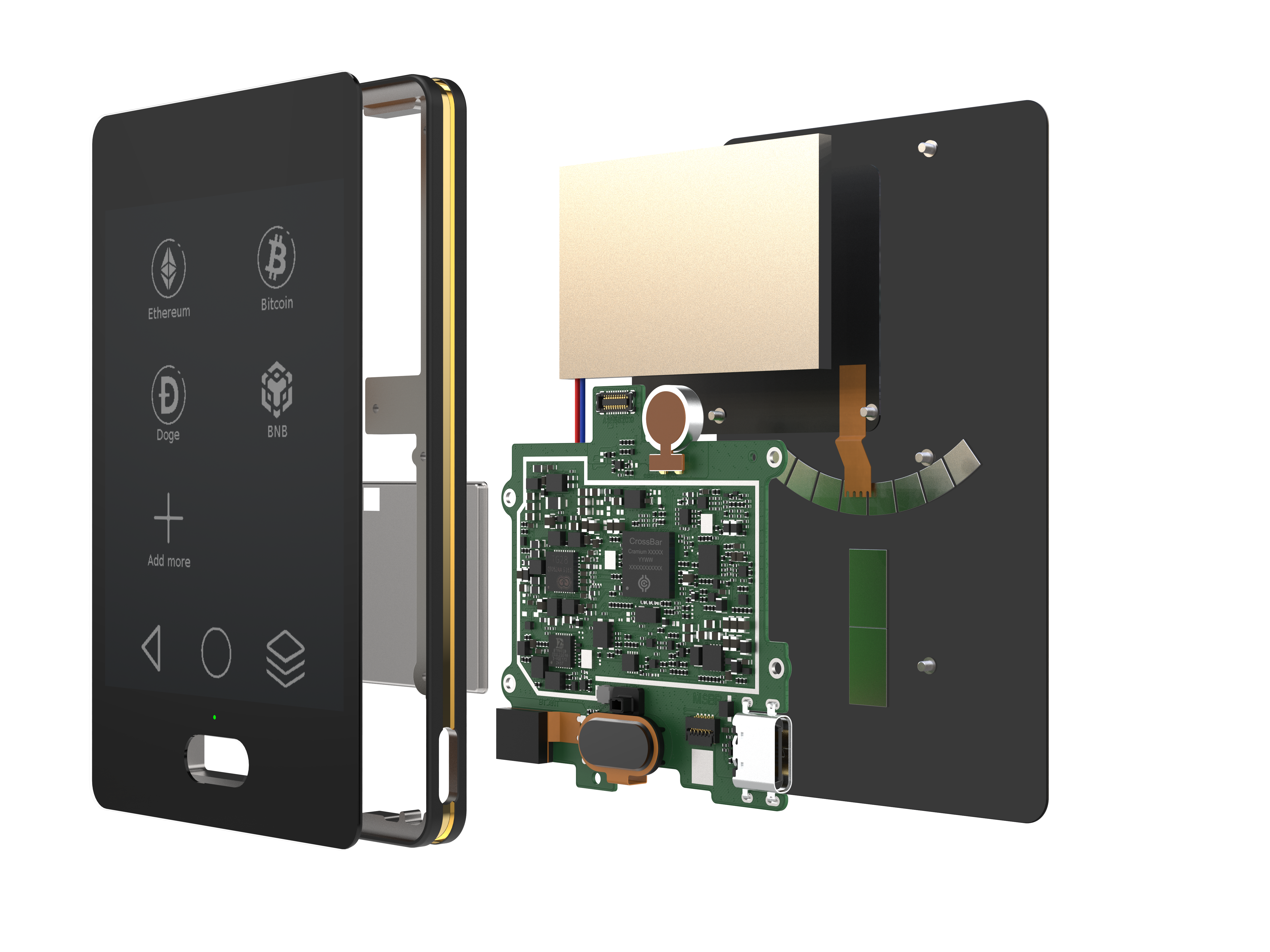
Hardware security techniques developed for modern chips — such as secure enclaves, tamper‑resistant packaging, and hardware‑based key isolation — can significantly improve the safety of cryptocurrency wallets. Most hardware wallets rely on generic secure elements and microcontrollers to store private keys, but chip‑level security can make attacks far more difficult.
Features like Physically Unclonable Functions (PUFs) can derive cryptographic keys unique to the silicon itself, preventing duplication or extraction even if the device firmware is compromised. Likewise, secure boot ensures the wallet only runs manufacturer‑signed firmware, while true random number generators (TRNGs) create strong private keys and transaction nonces. These chip‑based defenses reduce reliance on software patches and make physical or side‑channel attacks (e.g., power analysis or fault injection) much harder to execute.
For hardware crypto wallets, chip security also enables multi‑layered protection against real‑world threats. A dedicated secure element can encrypt and isolate private keys so they never leave the chip, even when connected to a potentially compromised host. Anti‑tamper sensors and epoxy coatings can raise the cost to disassemble or probe the device physically. Advanced chips also support trusted execution environments (TEEs), allowing transaction signing in an isolated zone beyond the purview of the host OS. For users, this translates into safer key management, reliable transaction signing, and resilience against both remote exploits and physical theft attempts.